The first ransomware for Apple OS X was recently discovered
IT experts from Palo Alto Networks company have found the first real ransomware for Apple OS X. The malware was named KeRanger and it is detected by antivirus software as OSX/Filecoder.KeRanger.A. KeRanger refers to the type of crypto-ransomware or filecoder and specializes in encryption of users’ files with the further demand of ransom for decryption.

To spread the infection cyber criminals have chosen an effective way to compromise distribution software called Transmission for OS X. This software is a simple freeware BitTorrent client. A few days ago, two distribution of Transmission v2.90 have been compromised by KeRanger and were distributed on the official website of the client. Since the Transmission is a freeware, cyber criminals could simply compile a special backdoored version and replace it on the server of developers. In addition, compromised legitimate distribution has been signed with a digital Mac developer certificate.
Since the file has a legitimate digital signature, malicious program could successfully bypass the security check software Apple Gatekeeper. After installing the compromised app, the malicious code is being activated on the user’s computer. After that, KeRanger waits for three days before connecting with its own C&C server, using the anonymous TOR network. This trick masks the presence of ransomware after compromising the user. After connecting to the C&C, KeRanger initiates the process of encryption of certain types of user files on the computer. To decrypt files, criminals demand ransom in amount of 1 Bitcoin (about $400). In addition to this, KeRanger tries to encrypt the backup file to prevent the user’s ability to recover from it.
As we already mentioned, the two compromised legitimate distributions have been signed with a digital certificate that was issued by Apple. Developer’s token in this digital certificate is “POLISAN BOYA SANAYI VE TICARET ANONIM SIRKETI (Z7276PX673), which is different from the same token used to sign the previous versions of legitimate Transmission software.
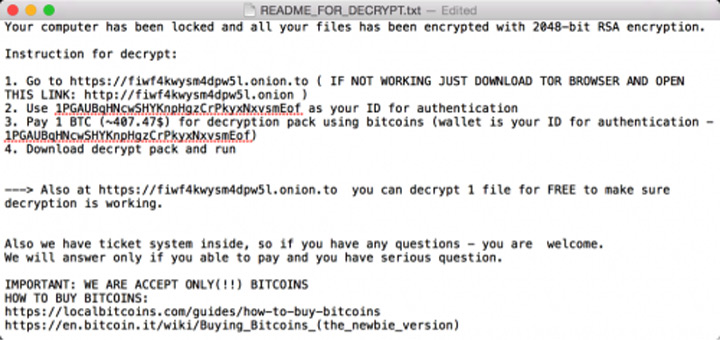
KeRanger ransomware encrypts, more than three hundred types of files, including the following: .doc, .docx, .docm, .dot, .dotm, .ppt, .pptx, .pptm, .pot, .potx, .potm, .pps, .ppsm, .ppsx, .xls, .xlsx, .xlsm, .xlt, .xltm, .xltx, .txt, .csv, .rtf, .tex, .jpg, .jpeg, .mp3, .mp4, .avi, .mpg, .wav, .flac, .zip, .rar., .tar, .gzip, .cpp, .asp, .csh, .class, .java, .lua, .db, .sql, .eml, .pem. Encrypted by KeRanger files receive additional .encrypted extension to an existing name. To encrypt files ransomware uses symmetric AES and asymmetric RSA encryption algorithms. To decrypt files user needs to get the RSA private key that can be used to decrypt the symmetric AES key, which is stored in the body of each file.
The digital certificate that was used to sign malicious files, already has been revoked by Apple, and protective software Gatekeeper already detects KeRanger files. Developers of the Transmission Project have also been notified of the incident and compromised distributions have been removed from the server. Apple added a signature to their KeRanger XProtect security tool, the appropriate update was automatically received by all Macs.
Related Posts
- Top websites were involved In large-scale Malvertising-campaign
- Trojan Acecard attacks applications of banks and financial systems
- 24 Ransomware were already created based on the open source malware Hidden Tear
- Oracle has released an emergency Java update for Windows
- Hackers have stolen 250 GB of data from NASA and attempted to crash $222m drone
- LeChiffre ransomware encryption was decrypted
- Schoolboy hacked email address and gained access to personal information of the head of US National Intelligence
- Recently found Trend Micro vulnerability allows any website to execute arbitrary Windows commands

This was very intuitive and helpful. Just make sure you follow each step in the correct order. It is time consuming, but very important. Thank you! – Jorma Filatov
I am so thankful for this guide. I was seconds away from formatting my hard drive on my laptop when I found this guide. It was totally free and easy to follow. Thanks from one happy guy and his malware free computer! – Lukas Foerster
Thanks! It works! – Michael S. Hardy
Works like a charm, thanks, you are the best! – Sari Tiilikainen