Trojan Acecard attacks applications of banks and financial systems
The experts from Kaspersky Lab published a report where they spoke about the evolution of the family of mobile Trojans called Acecard. The first samples of this malware were discovered in 2014, but today this family of malicious programs has gained significant momentum and is one of the most dangerous threats for mobile devices. For example, Acecard is responsible for almost all attacks using bankers in Australia.
Experts writing that during the study of the Trojan, they found that behind the creation of various Acecard modifications are standing the same authors who had previously developed Backdoor.AndroidOS.Torec.a – the first TOR Trojan for Android, and Trojan-Ransom.AndroidOS.Pletor.a – the first mobile ransomware. All malicious programs have similar lines of code and use the same command servers.
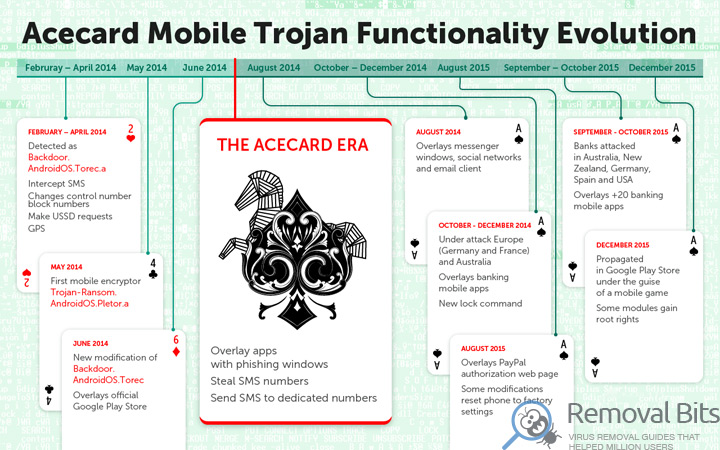
Acecard family is used for all sorts of attacks, but mainly focused on financial applications. For example, different versions of the Trojan attack nearly 50 financial applications (program-clients of global payment systems and banks) and services. This malware uses a variety of techniques – from stealing banking SMS, to overlapping official application windows with phishing messages. Also Acecard steals passwords from the 9 official social networking applications, and attacks the two banking applications to steal credit card data.
Experts traced all evolutionary chain of the Trojan, starting from Backdoor.AndroidOS.Torec.a, discovered in 2014. During that time malware has undergone several major transformations, eventually learning to block bank application and payment systems with phishing windows, to steal the passwords of social network accounts, intercept incoming SMS-messages, send SMS-messages, transfer all the data about the infected device to the remote servers of attackers, and even reset the mobile device to factory settings.
However, the peak of activity of Acecard began in June 2015. If earlier the experts were detecting from 2 to 5 files connected with the Trojan per month, starting from June, they began to find about 20 files per month. Simultaneously, the number of attacks has increased. Creators of the malware didn’t stop there, and the family continued to grow insanely. For example, today in almost all versions of Acecard there is a trigger, once activated the Trojan will cover any specified application with its own window. Also, malware developers have implemented a feature that allows them on command to lock victim’s device, for example, to demand a ransom.
Experts write that now the majority of attacks falls on Russia, Australia, Germany, Austria and France. In Germany and Australia Acecard Trojans are the most widespread, ahead of other mobile bankers.
December 28, 2015 experts from Kaspersky Lab found one of the modifications of Acecard (Trojan-Downloader.AndroidOS.Acecard.b) in the official app store Google Play Store. Malware were spreading disguised as a game, though the authors of Malware not even bothered to create at least some semblance of a legitimate application – the game wasn’t working, and after installation, on the victim’s screen were appearing an icon of Adobe Flash Player.
Today, the Acecard family uses almost all of the known distribution methods: malware are distributed under the guise of other programs through the official application store, as well as through other Trojans.
Related Posts
- Top websites were involved In large-scale Malvertising-campaign
- The first ransomware for Apple OS X was recently discovered
- 24 Ransomware were already created based on the open source malware Hidden Tear
- Oracle has released an emergency Java update for Windows
- Hackers have stolen 250 GB of data from NASA and attempted to crash $222m drone
- LeChiffre ransomware encryption was decrypted
- Schoolboy hacked email address and gained access to personal information of the head of US National Intelligence
- Recently found Trend Micro vulnerability allows any website to execute arbitrary Windows commands


This was fast, easy and found all of malware! Thanks a million! – Kiera Byrne
Thanks! It works! – Michael S. Hardy
Just great! This is a very helpful guide – Mikael Virtanen
– Mikael Virtanen
Thanks for taking the time to make this working guide. It was very helpful – Anne F. Gosselin